Single Sign-On Guide for Azure
Marigold ID supports Security Assertion Markup Language (SAML) Single Sign-On. This functionality streamlines user access by requiring a single authentication with your company’s IdP, granting access to Marigold ID and Marigold products without the need to manage additional credentials.
As a Marigold customer, you can configure SSO with Azure as described below.
Azure IdP Mapping
If your company is using Azure as your IdP, please follow the steps below to obtain the SAML certificate and metadata and pass them to your Marigold team.
-
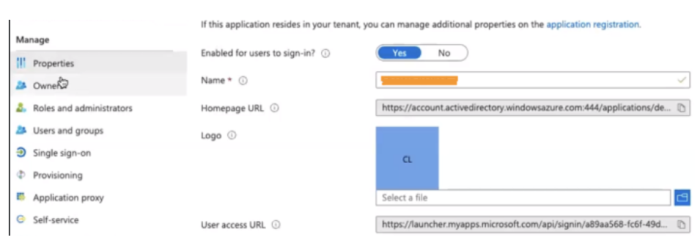
In Azure, create a "Marigold Id" Application.
-
Setup Single Sign-On by clicking App > Single Sign-on.
-
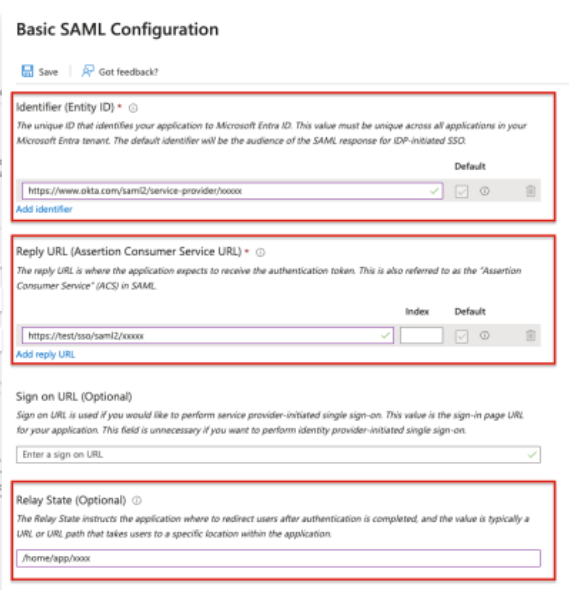
Configure the following values:
-
Identifier (Entity ID): <any URL>
-
Reply URL (Assertion Consumer Service URL): <any URL>
-
-
Configure Attributes and claims:
-
email: user.userprincipalname. The user.userprincipalname may vary depending on your settings. When configuring this attribute, confirm you are using the correct email attribute to ensure the submission of the correct email address. Azure employs various types of email variables, which may differ significantly from other platforms.
-
firstName: user.givenname
-
lastName: user.surname
-
-
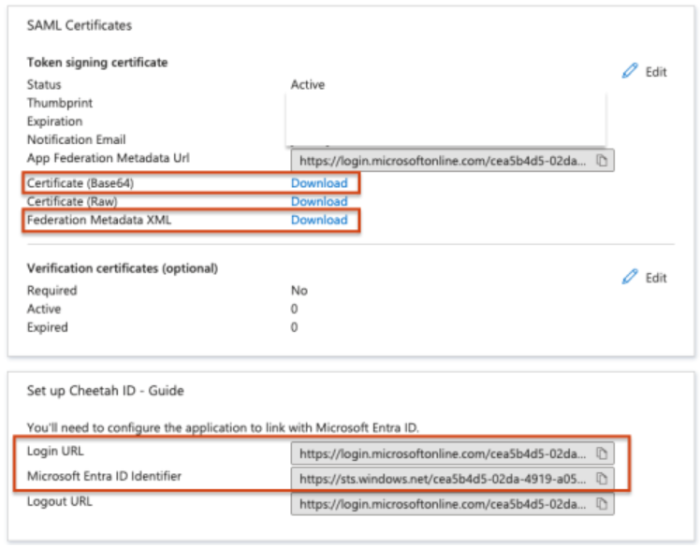
From the same Single Sign-on screen, note and pass the following details to your Marigold team:
-
Certificate
-
Federation Metadata XML
-
Login URL
-
Microsoft Entra ID Identifier
-
Once Marigold’s IdP is configured, your Marigold team will provide the Azure IdP Metadata and the information below for configuring your Identity Provider to communicate with the Marigold ID application.
| Client IdP | Marigold Values |
|
Single sign-on URL |
Assertion Consumer URL |
|
Audience URI (SP Entity ID) |
Audience URL |
|
Default Relay State |
Default Relay State URL |
Please note that the default RelayState is needed for your IdP to directly forward to the Marigold ID application when your user logs in to Marigold ID.
When the above is completed, please contact your Marigold team so that a meeting can be arranged to test the integration.
User Management
For organizations integrated with Marigold via Single Sign-On, all user management must be handled through your organization’s IdP. User accounts and access permissions should not be managed directly within the Marigold platform.
When a new user is provisioned in your IdP and assigned access to the Marigold application, the SSO integration will grant access based on the permissions defined in the mapped user groups.
Conversely, if a user is de-provisioned or removed from your IdP, the system will prevent them from accessing Marigold.
Please note that this approach represents a one-way user management flow. Your organization’s IdP acts as the single source of truth for managing user access to Marigold applications.
The platform supports two ways of assigning user access in Marigold ID:
-
Direct Assignment: Access is assigned at the individual user level (known as personal access).
-
User Group Assignment: Users are added to a user group that has predefined access. Any changes to the user group’s access will automatically apply to all users within that group.
Note: Both personal access and user group access can be assigned to a user simultaneously. The system will evaluate both and grant the user the highest level of access (i.e., the most privileged role) between the two.
If your organization has more than a handful of users (e.g., 10+), or you expect to scale access across departments or brands, utilizing user groups is the more efficient and scalable option.
Direct Assignment
Direct Assignment is ideal for assigning access to a small number of users without needing to configure or rely on user groups. This approach allows for customized permissions tailored to specific users based on their individual roles or responsibilities.
To add a user and grant them access to Marigold ID:
-
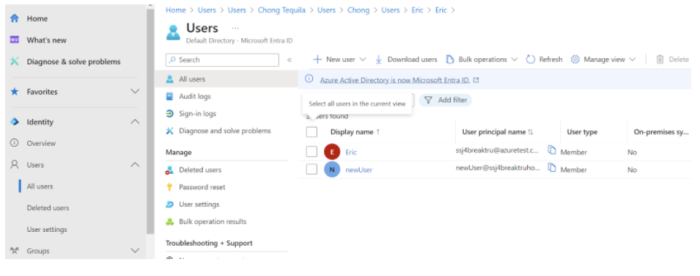
In Azure, select Users > All Users from the left navigation bar. The User Management page is displayed.
-
Click New User.
-
Enter the required user information and click Save. Make sure the correct domain is selected for the User Principal Name field.
-
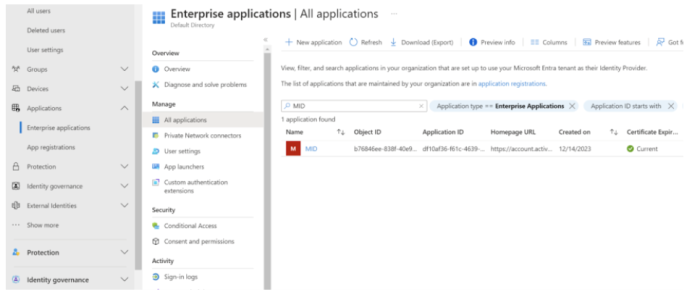
Assign the user to the Enterprise Application created to integrate with Marigold ID. Select Application > Enterprise Application from the left navigation bar.
-
Find and select the Marigold ID application from the application list.
-
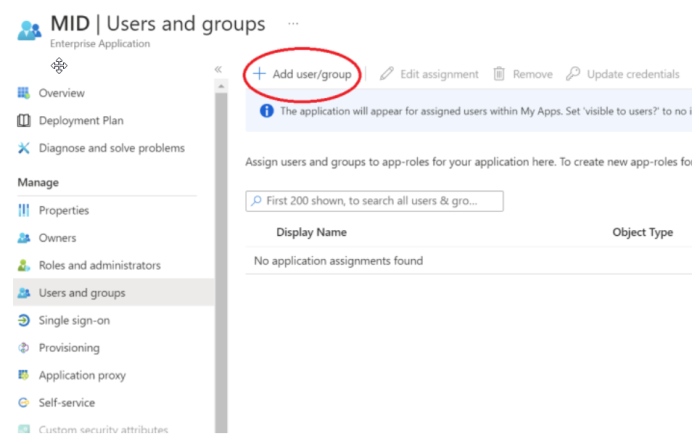
In the displayed application window, select Manage > Users and Groups.
-
Click Assign users and groups.
-
In the Users and Groups window, click Add user / group.
-
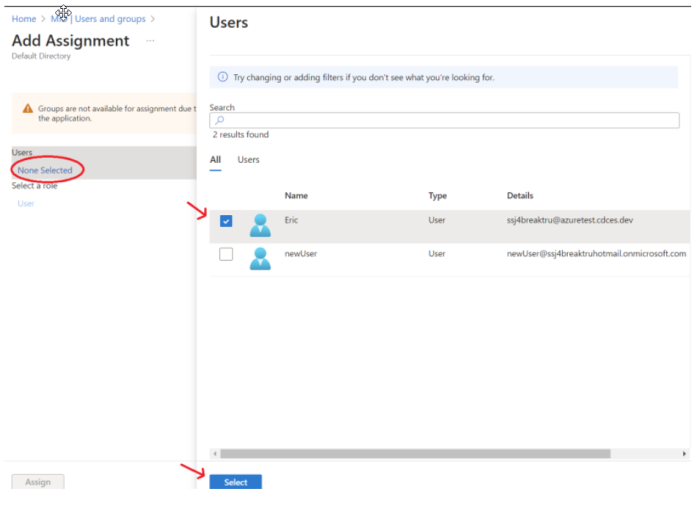
Click None Selected, then select the user to be added from the Users popup window, and click Select.
-
Click Assign to save the selection.
The user assigned to the application can now log in from the Azure domain, and they will see the Marigold ID application. Clicking the application will redirect the user to Marigold ID, where their account will be automatically created if it does not already exist.
User Group Assignment
To enable SSO to access Marigold products using Marigold ID’s User Groups, please note the following:
| Existing Client | New Client |
|
If you are an existing Marigold client using Cheetah Digital, (Undefined variable: MyVariables.Product_Loyalty_Short), and/or Platform, before the migration: If you currently have an active SSO integration with a Marigold product, your Marigold team will export the list of existing users along with their current permissions. Please review the exported user access and inform the Marigold team of the User Groups and related access / permissions that need to be created. Please note the criteria for group name creation as below:
For example: org-admin-all-applications, standard-user, report-viewer Your Marigold team will set up these User Groups for your organization. You will then need to map them to the corresponding user groups in your Identity Provider to complete the SSO setup. |
If you are a new Marigold client, or if your company has not previously integrated SSO with any Marigold products, please inform your Marigold team of the User Groups and access levels that need to be created. Please note the criteria for group name creation as below:
For example: org-admin-all-applications, standard-user, report-viewer Your Marigold team will set up these User Groups for your organization. You will then need to map them to the corresponding user groups in your Identity Provider to complete the SSO setup. |
Configure Custom Groups in Azure
Once the User Groups are created by your Marigold team in Marigold ID, follow these steps to create the same groups in your organization’s Azure IdP.
-
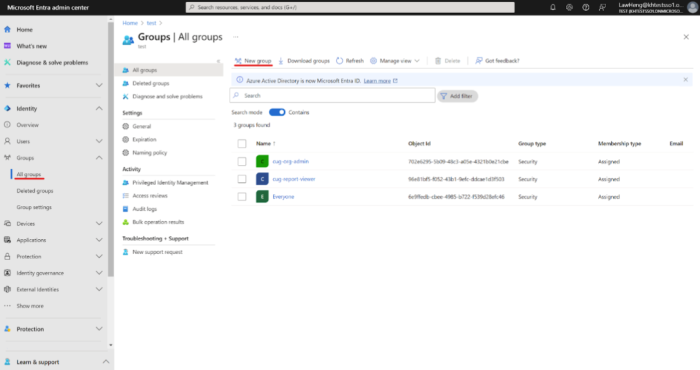
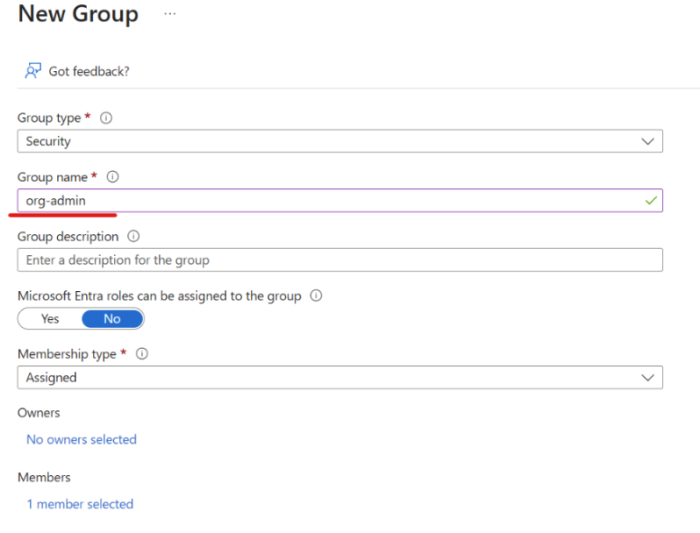
Navigate to Azure Groups and click New Group.
-
Enter a name for the new Group. This Group name should be the name of the User Group, in all lowercase, without any spaces. For example: "org-admin."
-
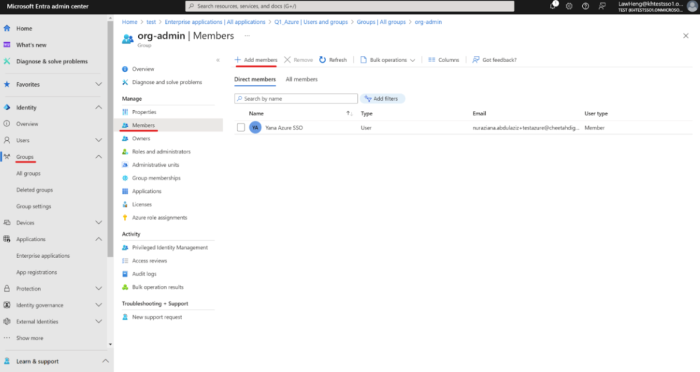
Click Add Members to assign users to the new Group.
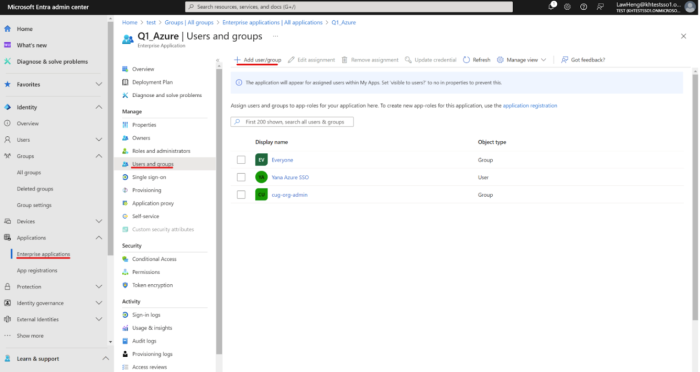
-
Assign the Group to the Enterprise Application.
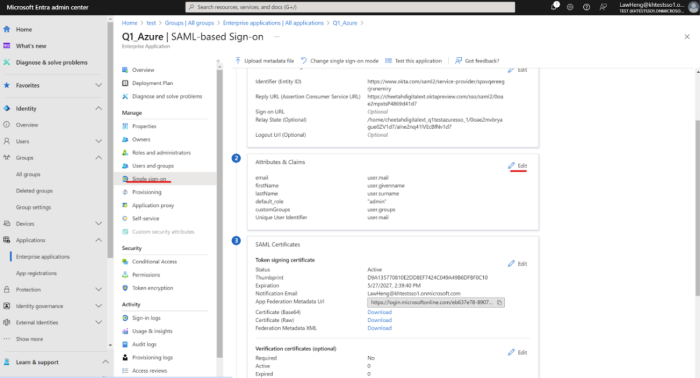
-
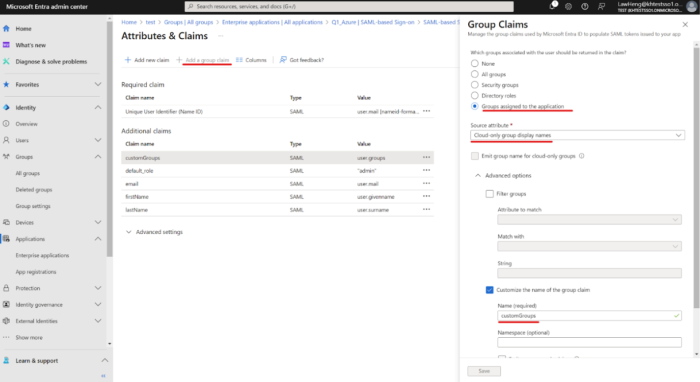
Create the customGroup claim.
-
Enter the following required Claims (on top of existing group)
-
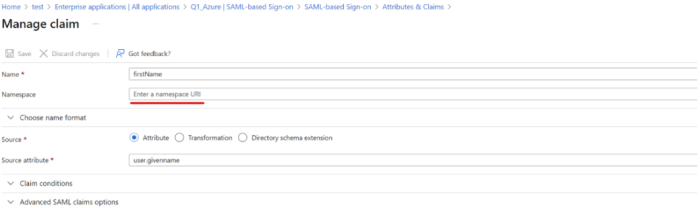
firstName: user.givenname
-
lastName: user.surname
-
email: user.mail
-
Unique User Identifier: user.userprincipalname
-
customGroups (group claims)
-
-
Remove the namespace for the claims.
-
Enter CustomGroups Claims Requirements:
-
Group associated: Select Groups assigned to the application
-
Source attribute: Select Cloud-only group display names
-
Name: Should be customGroups
-
Configure and Maintain User Groups in Marigold ID
Once onboarded to Marigold ID, your Organization Administrator can access the Marigold ID Administration environment and verify the User Groups created by your Marigold team.
If you need to create additional User Groups within Marigold ID, please see Create a User Group for more information on this process. Please note the following when creating a User Group in Marigold ID:
-
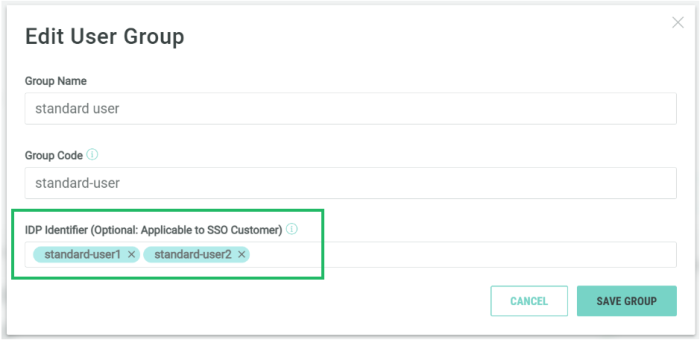
The Marigold ID Group Name field must match the Group name in your IdP.
-
Leave the IDP Identifier field empty.
For any new User Groups created, be sure to map them to your organization’s IdP groups. This mapping ensures that users can be assigned to the appropriate groups through your IdP.
Once you create and save a new User Group, any users add to the User Group will automatically be granted access to the Business Units and applications defined for that User Group.
IdP Identifier
By default, the IDP Identifier field is left empty; as a result, users can be mapped to this User Group only based on the Group code. Optionally, you can use the IDP Identifier field to associate multiple group names with a specific User Group for more flexible user mapping.
User Group Synchronization
The platform supports two options for synchronizing User Groups in Marigold ID with Groups in Azure. For information on these options, please see Manage SSO User Group Synchronization .
Application Specific User Group Mapping
For the Cheetah Digital, Marigold Grow, and (Undefined variable: MyVariables.Product_Loyalty_Full) applications, Marigold ID allows Organization Administrators to assign permissions specific to those applications.
For more information on integrating with Cheetah Digital, please see Map a User Group to an Engage+ Access Group.
Marigold ID integrates with Marigold Grow and (Undefined variable: MyVariables.Product_Loyalty_Full) using a feature called App Attributes. This option allows Organization Administrators to manually select the desired application-specific Role to which users in this User Group will be assigned, and also to customize the privileges granted to the user by that Role. See Configure Application Role for a User Group for more information.