SSO
What is SSO
Single sign-on (SSO) is an identification method that enables users to log in to multiple applications and websites with one set of credentials. SSO streamlines the authentication process for users.
SSO through SAML
Liveclicker supports Secure Assertion Markup Language (SAML), which allows you to provide single sign-on (SSO) for your Liveclicker account using enterprise identity providers such as Active Directory, OKTA and LDAP (SAML2.0 is supported for user SSO login). Implementing single sign-on via SAML means that the sign in process and user authentication are handled entirely outside of your Liveclicker account. Your SAML enabled users will not directly visit the usual Liveclicker login page to sign in. Instead users sign in to the corporate system (authenticated by Active Directory or LDAP for example) and click a link to access Liveclicker and are automatically signed in. No need to enter separate sign-in credentials for Liveclicker.
After you've enabled SAML (by building a SAML server yourself or by using one of the SAML services), all user management and authentication is handled outside of Liveclicker. However, changes made outside of your Liveclicker account are immediately synced back to Liveclicker. For example, if you add a user in your internal Active Directory or LDAP authentication system, the change is synced back through your SAML provider and the user is added to your Liveclicker account. If you delete a user in your system, the user will no longer be able to sign in to Liveclicker (though their account will still exist in Liveclicker).
The only user data that is stored in Liveclicker is the user name and email address. However, you can also choose to sync the following user data: first name, last name, email, phone number. You do this with by adding these attributes to your SAML assertion code. See User attributes that can be set in SAML. Liveclicker does not store user passwords.
How SAML for Liveclicker works
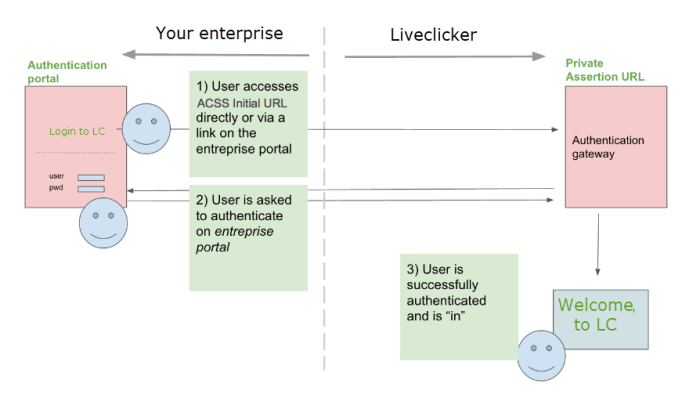
SAML for Liveclicker works the way SAML does with all other service providers. The typical use case is that your users belong to a corporation and all user authentication is managed by your corporate authentication system (for example, Active Directory or LDAP), which is referred to generically as an identity provider (IDP). The service provider (SP), in this case Liveclicker, establishes a trust relationship with IDP and allows that external IDP to authenticate users and then seamlessly sign them in to Liveclicker. In other words, a user signs in at work and then has automatic access to the many other corporate applications such as email, your CRM, and so on without having to sign-in separately to those services. Aside from the convenience this provides to users, all user authentication is handled internally by a system that you have complete control over.
After you've enabled SAML as the type of single sign-on for your Liveclicker, users who visit Liveclicker account and attempt to sign in are redirected to your SAML server for authentication. Your users' identities can be stored either on the SAML server or can be validated by an identity directory such as Microsoft Active Directory or LDAP. Once authenticated, users are redirected back to Liveclicker and automatically signed in.
Before you start
To set up SAML in your Liveclicker, you'll need the following:
-
A SAML server with provisioned users or connected to an identity repository such as Microsoft Active Directory or LDAP.
-
The Remote Login URL for your SAML server (sometimes called SAML Single Sign-on URL).
-
The SHA1 or SHA2 fingerprint of the SAML certificate from your SAML server. X.509 certificates are supported and should be in PEM or DER format. There is no upper limit on the size of the SHA fingerprint.
After you have your SAML server properly configured, you use the remote login URL and the SHA fingerprint to configure SAML within Liveclicker. In addition, you MUST provide the following parameters for users signing in via SAML:
- firstname — non empty string.
- lastname — non empty string.
- email — non empty string.
- phone — non empty string.
- external_id — user id from your system if your users are identified by something other than an email address, and if their email addresses are subject to change. Specified as a string.
- role_id — must be either 1 or 3 (1 is admin, 3 is contributor).
Enabling SSO using SAML in Liveclicker
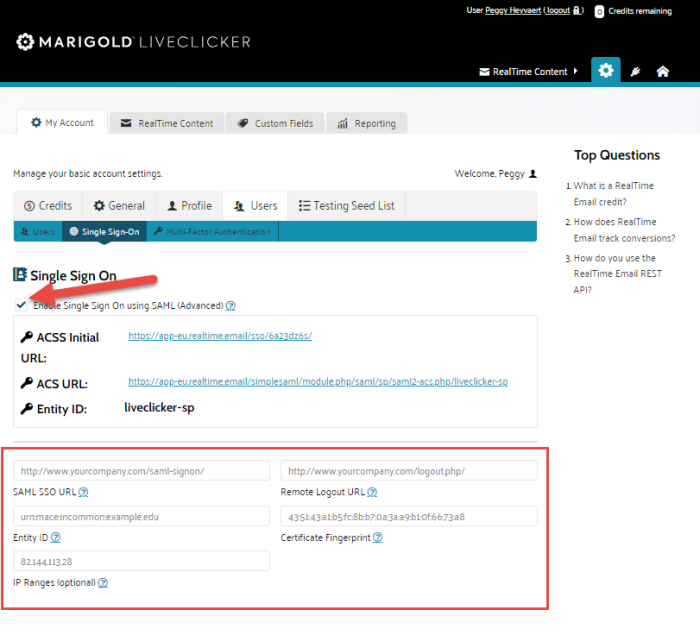
1. Go the account settings section in Liveclicker and go to the Users tab.
2. Check the option Enable Single Sign On using SAML. You need to reconfirm your password.
3. In the additional fields displayed below, enter all the information collected in Before you start.
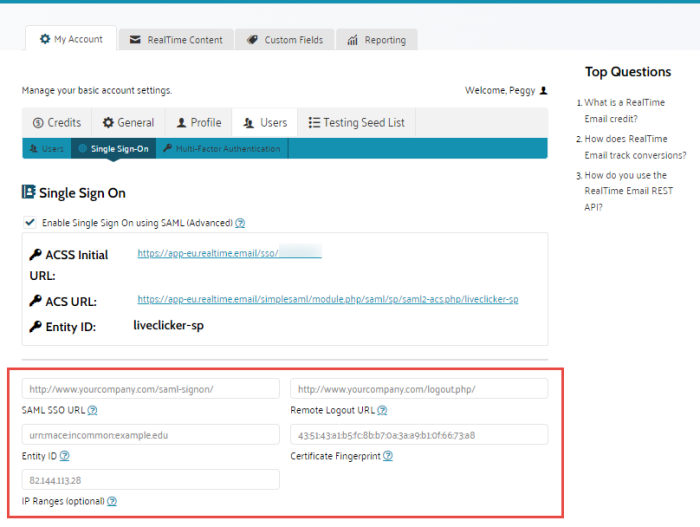
- SAML SSO URL — The URL invoked by Liveclicker to redirect users to your identity provider.
- Remote Logout URL — The URL users are redirected to by Liveclicker when logging out.
- Entity ID — Unique ID of the SAML entity, whether this is an IDP or a Service Provider.
- Certificate fingerprint — The SHA1 fingerprint of the SAML certificate.
- IP Ranges — If left empty, all requests are routed through remote authentication. If filled out, only requests from the given IP ranges will be routed through remote authentication. All other requests will be routed to the normal login form.
SSO setup for Okta IDP
Liveclicker supports single sign-on (SSO) for your Liveclicker account using enterprise identity provider OKTA.
Below you will find the steps to configure this on OKTA’s end as well as in Liveclicker.
OKTA Configuration
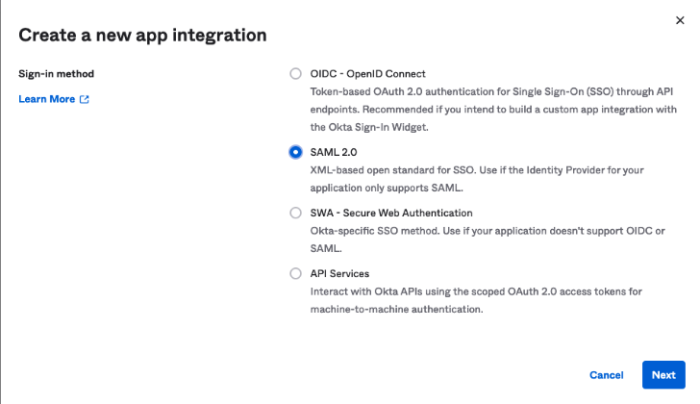
1. First click on Create App Integration to create a new integration and select SAML 2.0
2. Once you select the SAML method, you need to configure some parameters with the following values:
-
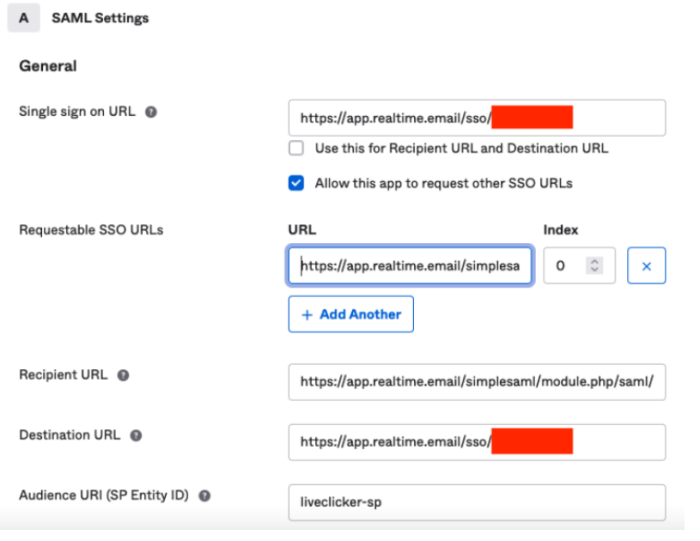
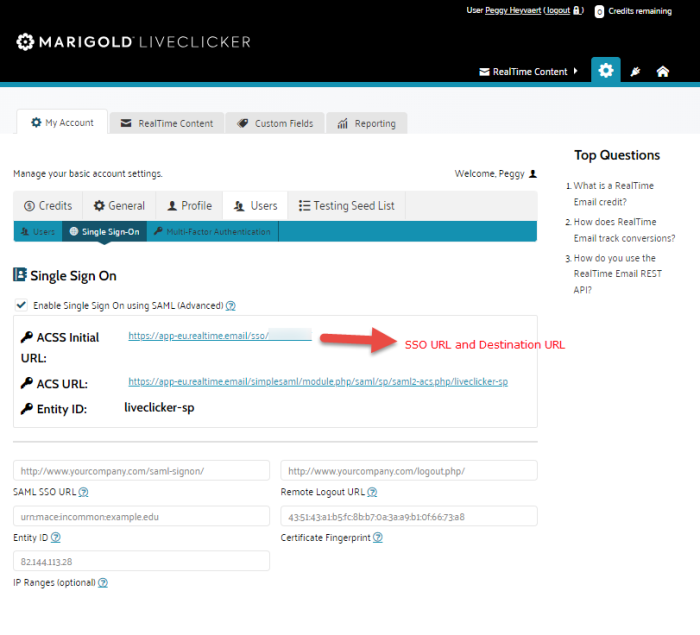
Single sign-on URL — In your Liveclicker account, under Account Settings -> Users -> Single Sign On, you will find the sign-on URL, which is a unique account URL as ACSS Initial URL.
-
Requestable SSO URLs — https://app.realtime.email/simplesaml/module.php/saml/sp/saml2-acs.php/liveclicker-sp
-
Destination URL — Same as Single sign-on URL.
-
Audience URI (SP Entity ID) — liveclicker-sp
3. You should also enable the checkbox Allow this app to request other SSO URLs.
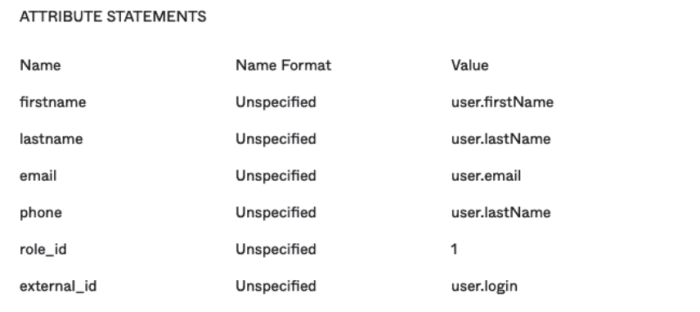
4. Next, configure all Attribute statements. It’s important to have all the attributes/parameters configured. The most important one is role_id, if you don't have a way to match it on your end, it will need to be hardcoded.
- firstname — non empty string.
- lastname — non empty string.
- email — non empty string.
- phone — non empty string.
- external_id — user id from your system if your users are identified by something other than an email address, and if their email addresses are subject to change. Specified as a string.
- role_id — must be either 1 or 3 (1 is admin, 3 is contributor).
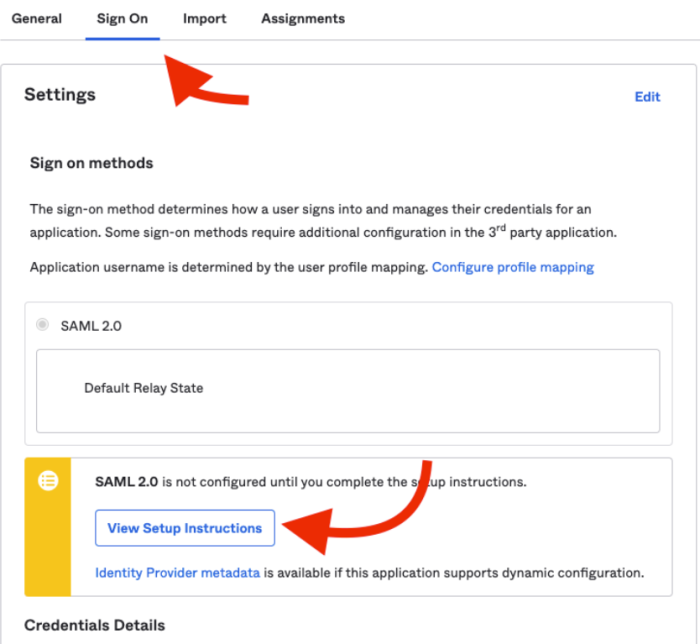
5. Once the previous steps are completed, you will be redirected to the Sign On tab, where you will find a button View Setup Instructions. There you will find the information you will need to finish the SSO setup in the Liveclicker platform.
Liveclicker Configuration
In order to finish the SSO configuration, you will need to add some parameters in the Liveclicker platform under Account Settings -> Users -> Single Sign On.
- SAML SSO URL — The URL invoked by Liveclicker to redirect users to your identity provider. This should match the Okta Identity Provider Single Sign-On URL.
- Remote Logout URL — The URL users are redirected to by Liveclicker when logging out. This should match the Okta Logout URL.
- Entity ID — Unique ID of the SAML entity, whether this is an IDP or a Service Provider. This should match the Okta Identity Provider Issuer.
- Certificate fingerprint — The SHA1 fingerprint of the SAML certificate. This should match the Fingerprint (SHA-1) that you can get from the certificates in OKTA. You need to insert “:” every 2 characters.
- IP Ranges — If left empty, all requests are routed through remote authentication. If filled out, only requests from the given IP ranges will be routed through remote authentication. All other requests will be routed to the normal login form.